What Is The Punycode Phishing Attack And How To Stay Safe
The internet can be a dangerous place. Earlier this week, we talked about a new scam email going around trying to get users to buy a fake VPN service. The scam put your money and your data at risk. Fortunately for the diligent, there are ways to spot a scam like that. Not all scams are easy to spot though, and phishing scams have just gotten smarter thanks to a little thing called Punycodes. It’s a new way to register domains and while it wasn’t developed to scam people, it is being used to do. Here’s a look at what the Punycode phishing attack is, and how to stay safe.
Phishing Attacks
A phishing attack is when some creates a malicious website and makes it look like one you trust. For example, someone might replicate the Google or Facebook sign in page down to the T. If you don’t look at the URL you’ve typed, or have been redirected to, you will think you’re on the right page. You’ll enter you log in information and just like that, you’re information is stolen.
The internet is pretty mature now and web browsers come with excellent security. If you visit a shady website, your browser will tell you the website probably isn’t the one you’re looking for. Phishing attacks are also common knowledge so the average user knows to be careful.
Punycode Domains
The Punycode domain registration lets people register domains with foreign i.e. non-English characters in the name. The concept isn’t bad. You can take a character from a foreign language and using Punycode, convert it into a ASCII characters. If someone in China were to register a domain useful specifically for people in China, it’s better to have the domain name in Chinese. It makes the website name easier to remember if nothing else.
Punycode Phishing Attack
Punycode will convert domains in foreign languages, or domains using foreign characters, into ASCII characters. Unfortunately, when it does that, the ASCII character the foreign character is converted to uses a subset of ASCII characters. These subset characters are indistinguishable from regular English characters.
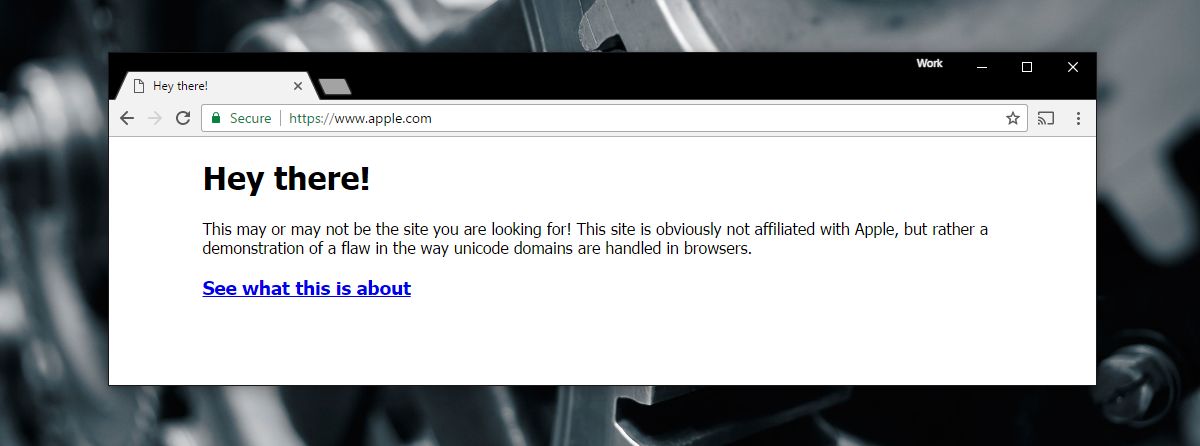
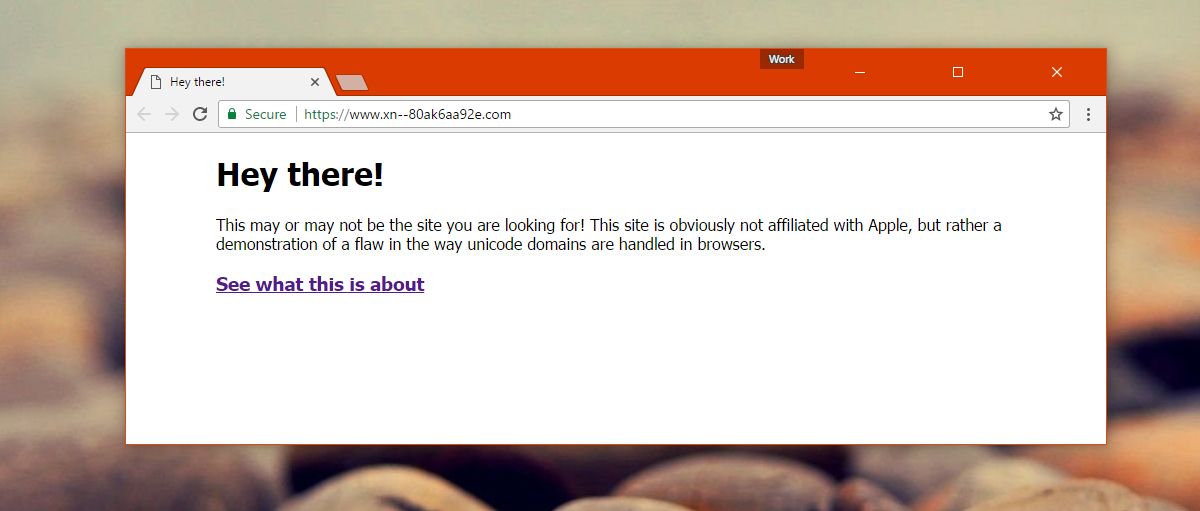
Case in point, this sample website developed by Xudong Zheng to show a Punycode phishing attack. It looks like you’re visiting Apple’s website because the URL clearly reads apple.com. It doesn’t tell you that the actual website URL is this: www.xn--80ak6aa92e.com
Xudong Zheng discovered this could be used as a phishing attack and wrote extensively about it, explaining how foreign character domains can be used to mimic the URL of popular websites.
Who Is At Risk
The following browsers are at risk;
- Chrome 57 and older versions
- Firefox
- Internet Explorer if you have additional language packs, particularly those for Russian installed
- Opera
Who is Safe
Users of the following browsers appear to be safe;
- Microsoft Edge
- Safari
- Internet Explorer if you only have the English language installed on your system
How To Stay Safe
As you can see from the at-risk browsers list, two popular web browsers are on it. Chrome and Firefox are both affected, as is Opera.
For Chrome users, there’s good news. To stay safe, all you have to do is update Chrome to version 58. Versions 57 and older are prone to this bug.
Version 58 has a fix and it’s now out on the stable channel.
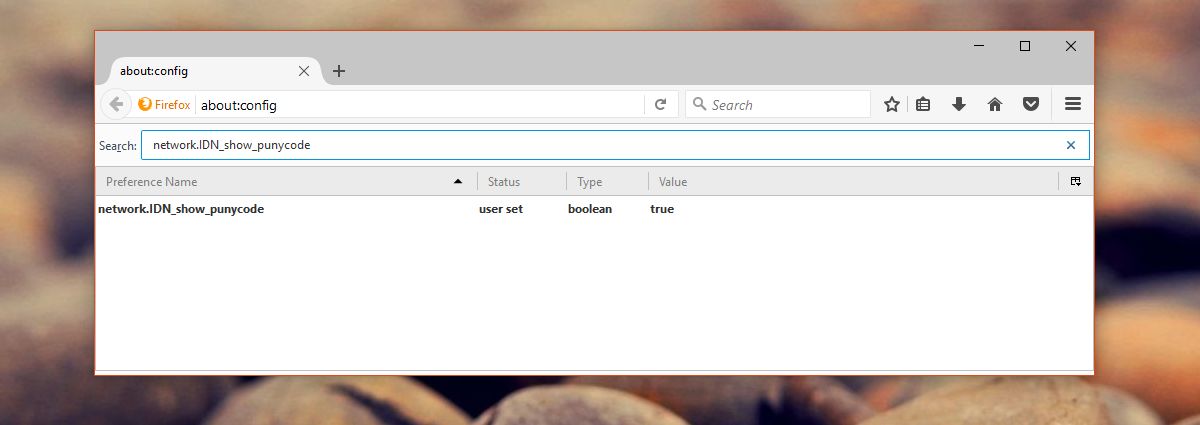
For Firefox users, there is a preference they can modify. Open Firefox and go to the about:config page. Search for the following preference. Double-click it to set its value to True.
network.IDN_show_punycode
Opera doesn’t have a solution out yet. If you know an extension that can fix this problem in Opera, let us know in the comments and we’ll add it.
Password Managers
Xudong Zheng suggests using Password managers to stay safe. Password managers automatically detect the domain you’re on, and offer to fill in your login information. You browser might be fooled by the domain but the password manager will not be. If it doesn’t offer to fill in your login information, there’s a good chance you’re on the wrong website.
