What Is Tor Project And How Tor Works [Complete Guide]
For anyone serious about internet anonymity and privacy, the Tor project would not be a new name. It is one of the few techniques/methods out there that provide anonymity in the real sense of the word, providing secure, almost-untraceable access to internet locations through layers and layers of routing. However, many users get confused by terminology used in such discussions, or are not aware of what the Tor project really is. In this article, I will attempt to explain as simply as possible what Tor project is, how it works and why should you use it.
WHAT IS TOR?

Tor project and all associated software are open source, and the network is free of charge.
SO, ONION ROUTING, EH?
Yup, you’re reading it right, it is called Onion routing actually. The technology behind onion routing involves multiple relay routers that only know the location, or internet address, of the last connecting router and nothing behind it. All they receive is the immediate sender location with an encrypted message telling the relay router the address of the next node. These relay routers are run by volunteers in various locations, and since no intermediate router (called as Tor, or Onion nodes) knows anything about the signal generating machine, it ensures anonymity as much as you can imagine over the internet. By keeping the entry points to the network hidden and encrypted, Tor ensures that no surveillance and traffic analysis method can identify the actual two computers that communicate.
Now, the big question remains: why is it called Onion routing? Basically this technique was designed for anonymous communication over networks, and involves multiple routers that process an encrypted message. Just like an onion is layers over layers, the encrypted message that Onion routers process is peeled off layer after layer, and each new layer tells the router the location of the next recipient – hence the term. This prevents the intermediary nodes from knowing the origin, destination and contents of the message.
Interestingly, Tor Project was initially an acronym for ‘The Onion Routing Project’. However, the project now does not identify itself as an acronym, hence no capitalization.
HOW TOR WORKS?
The following three graphics, taken from the Tor Project website itself, explain the process fairly easily.
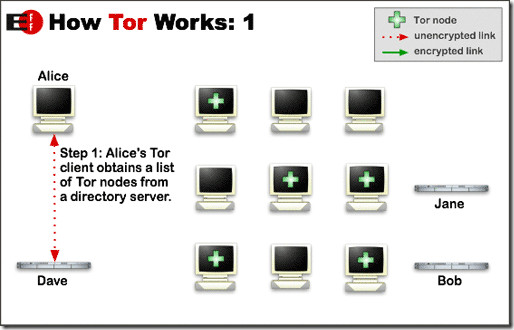
First, the client’s Tor-enabled software determines the list of available Tor nodes that are present in the network. By doing so, it ensures a random node selection each time so that no pattern can be observed by anyone spying, ensuring that you remain private throughout your activities. Random path selection also leaves no footprints, as no Tor node is aware of the origin or destination other than the terminal ones receiving from the clients. And since, from the millions of Tor nodes available, any one can act as the first receiving node, therefore it is virtually impossible to trace the origin.
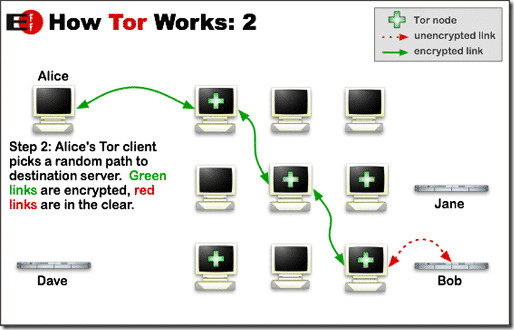
Now, the client generates an encrypted message which is relayed to the first Tor node. The Onion router on this node would peel off one layer of encryption and read the information identifying the second node. The second node would repeat the same process and pass on to third. This would go on until the final node receives the location of the actual recipient, where it transmits an unencrypted message to ensure complete anonymity.
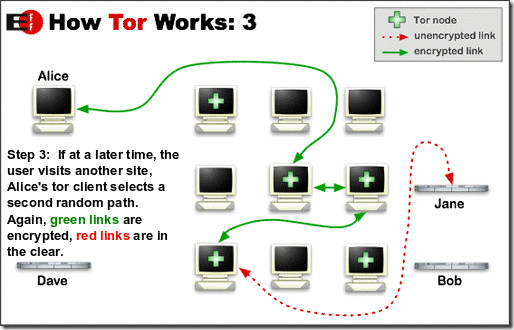
Finally, when the client computer wants to establish another path, suppose to visit another website, or even the same one, the Tor network will select an entirely different, random path this time.
SOUNDS GREAT, SO HOW CAN I USE IT?
Tor Project clients are available for almost all platforms, including Windows, Mac OS X and Linux. It is also available for major smartphones like Android, iOS and Nokia’s Maemo OS. Since the project is open source, you can also grab the source code from its website.
As Tor project itself puts it, Tor is not just a software that you can install and use – it’s more like an internet lifestyle, requiring you to change your browsing habits, reconfigure software, pay more attention to security etc. In the end, if you’re really serious about privacy and anonymity online, it’s all worth it. Give it a try if you like, and let us know what you make of the former ‘Onion routing’ project.

Nice article, except for 1 thing
Tor is good for ANONYMITY, but not PRIVACY
in fact Tor strips privacy from the internet, but that’s what gives it very good anonymity
The reason why Tor strips privacy is mainly the fact that all of your data is sent through 3 (or more) unknown computers. Especially because the traffic is decrypted for the exit node, everything you send through Tor should be considered as “sniffed” (or in other words, someone is watching what you browse)
While they are unable (or maybe able depending on how Tor’s encryption works) to find the source computer, they are able to log all the data that is sent from it.
Therefore, whenever you log on to a site, etc, the Tor exit node could be logging your credentials.
To learn more, read this:
http://www.wired.com/politics/security/commentary/securitymatters/2007/09/security_matters_0920
“The Onion router on this node would peel off one layer of encryption and read the information identifying the second node. ” Does not peal off all encryption corresponding to the payload.
Nice article.
For readers interested in this project please consider setting up a node (relay) on your own computer. The more relays the faster Tor will be. You decide how much of your bandwidth Tor may use. Guide here: https://www.torproject.org/getinvolved/volunteer.html.en